Imagine being able to access your devices from anywhere in the world with just a few clicks. Sounds like a dream, right? Well, with SSH device from anywhere login, that dream becomes a reality. Secure Shell (SSH) is more than just a protocol; it’s your key to unlocking seamless remote access. Whether you’re a tech enthusiast, a remote worker, or a business professional, SSH offers a secure way to connect to your devices no matter where you are. So, buckle up because we’re diving deep into the world of SSH and showing you how it can revolutionize the way you work and manage your digital life.
SSH isn’t just about logging in remotely; it’s about doing so safely. In today’s interconnected world, security is paramount. With cyber threats lurking around every corner, knowing that your connections are encrypted and protected is a game-changer. This guide will walk you through everything you need to know about SSH device from anywhere login, from setting it up to troubleshooting common issues. By the time you finish reading, you’ll be a pro at remote access.
But why stop at the basics? We’ll also explore advanced techniques and tips to enhance your SSH experience. From automating tasks to securing your connections with two-factor authentication, this article has got you covered. So, whether you’re a beginner looking to understand SSH or an experienced user wanting to refine your skills, you’re in the right place. Let’s get started!
Read also:When Is Kat Timpf Due The Inside Scoop Youve Been Waiting For
Table of Contents
- What is SSH and Why Should You Care?
- How Does SSH Work?
- Setting Up SSH for Remote Access
- Securing Your SSH Connections
- Advanced SSH Techniques
- Troubleshooting Common SSH Issues
- Alternatives to SSH
- Benefits of Using SSH for Remote Login
- SSH Device from Anywhere Login Explained
- Wrapping It All Up
What is SSH and Why Should You Care?
Let’s start with the basics. SSH, or Secure Shell, is a cryptographic network protocol that allows you to securely access a remote computer or server. Think of it as a digital handshake that ensures your data stays private and protected while traveling across the internet. But here’s the kicker—it’s not just about security. SSH also gives you the power to execute commands, transfer files, and even set up tunnels for other applications. It’s like having a Swiss Army knife for remote computing.
So, why should you care? In today’s fast-paced world, being able to access your devices remotely can save you time, money, and a whole lot of headaches. Whether you’re troubleshooting a server issue from the comfort of your home or accessing important files while on vacation, SSH makes it possible. Plus, with the rise of remote work, SSH has become an essential tool for many professionals. It’s not just for IT geeks anymore; it’s for anyone who wants to stay connected and productive.
Why SSH is a Game-Changer
- Secure connections that protect your data from prying eyes.
- Easy-to-use tools that don’t require advanced technical skills.
- Compatibility with a wide range of devices and operating systems.
- Cost-effective solution for businesses and individuals alike.
How Does SSH Work?
Now that you know what SSH is, let’s talk about how it works. At its core, SSH uses a combination of encryption, authentication, and data integrity checks to ensure secure communication between two devices. Here’s a quick breakdown:
- Encryption: SSH encrypts all data transmitted between your local machine and the remote device, making it nearly impossible for hackers to intercept and read your information.
- Authentication: Before you can access a remote device, SSH verifies your identity using either a password or a public key. This ensures that only authorized users can gain access.
- Data Integrity: SSH checks the integrity of the data being transmitted to ensure that it hasn’t been tampered with during transit.
Think of it like sending a letter in a locked briefcase. The briefcase (encryption) protects the contents of the letter, the lock (authentication) ensures that only the intended recipient can open it, and the tamper-proof seal (data integrity) guarantees that the letter hasn’t been altered. Pretty cool, right?
SSH in Action
Let’s say you’re working on a project and need to access a file stored on a remote server. With SSH, you can open a terminal on your computer, enter a few commands, and voilà—you’re connected. From there, you can navigate the server’s file system, run scripts, and even edit files as if you were sitting right in front of the machine. It’s like having a virtual office that you can carry with you wherever you go.
Setting Up SSH for Remote Access
Ready to get started? Setting up SSH for remote access is easier than you might think. Here’s a step-by-step guide to help you get up and running:
Read also:What Is The Salt Penis Trick A Deep Dive Into The Viral Sensation
Step 1: Install SSH
Most modern operating systems come with SSH pre-installed, but if yours doesn’t, don’t worry. You can easily download and install it. For Windows users, you’ll need to enable the OpenSSH client through the settings menu. For macOS and Linux users, SSH is usually ready to go out of the box.
Step 2: Generate SSH Keys
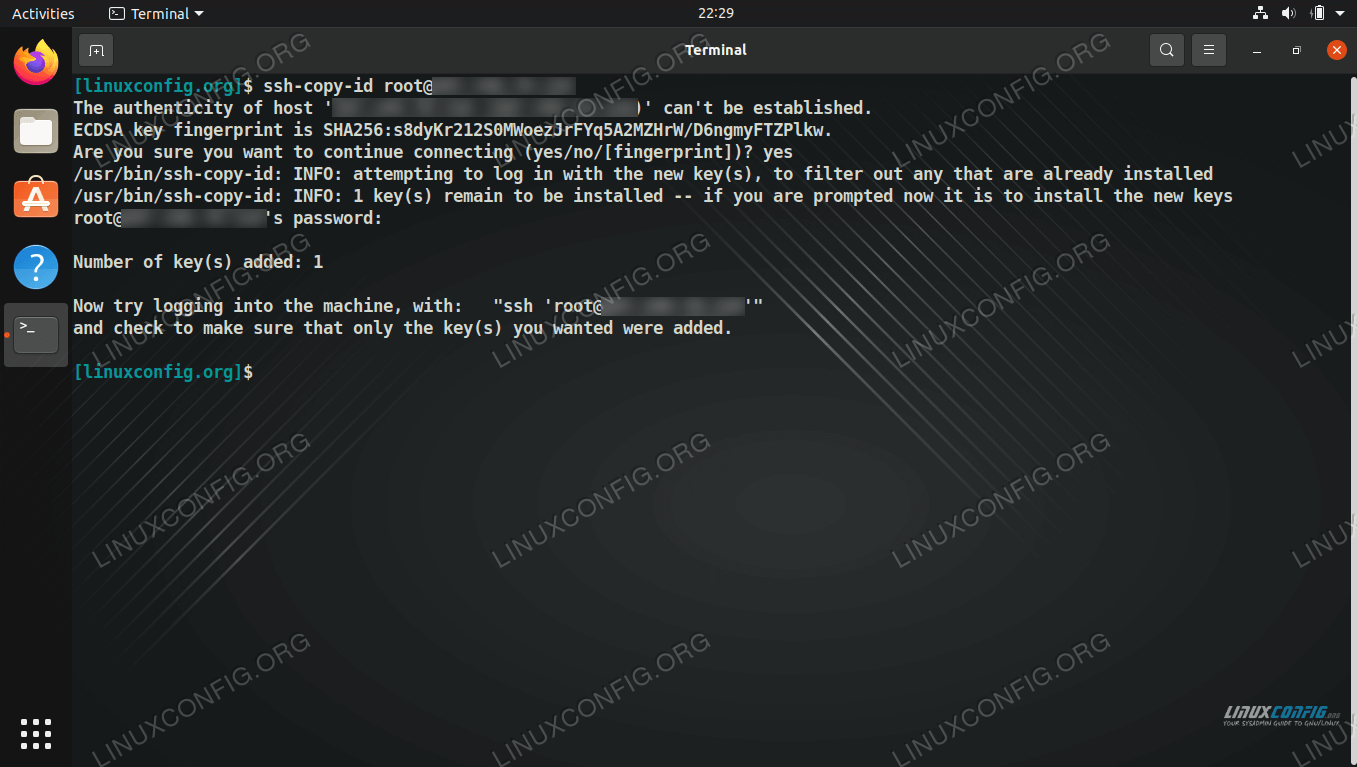
Instead of relying on passwords, which can be insecure, SSH keys provide a more robust form of authentication. To generate a key pair, open your terminal and type:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
This will create a public and private key. Keep your private key safe and share the public key with the remote server.
Step 3: Connect to the Remote Device
Once your keys are set up, connecting to a remote device is as simple as typing:
ssh username@remote_device_ip
Replace "username" with your actual username and "remote_device_ip" with the IP address of the remote device. If everything is configured correctly, you should now have access to the remote machine.
Securing Your SSH Connections
While SSH is inherently secure, there are a few extra steps you can take to further protect your connections. Here are some tips:
- Disable Password Authentication: Switch to using SSH keys instead of passwords to reduce the risk of brute-force attacks.
- Use a Non-Standard Port: Change the default SSH port (22) to something less obvious to deter automated attacks.
- Implement Two-Factor Authentication: Add an extra layer of security by requiring a second form of verification, such as a one-time code sent to your phone.
By following these best practices, you can ensure that your SSH connections remain secure and protected from potential threats.
Common Security Pitfalls to Avoid
Even with all these precautions, it’s important to be aware of common security pitfalls. For example, never share your private key with anyone, and make sure to regularly update your SSH software to patch any vulnerabilities. Staying vigilant is key to maintaining a secure environment.
Advanced SSH Techniques
Once you’ve mastered the basics, it’s time to take your SSH skills to the next level. Here are a few advanced techniques to consider:
SSH Tunneling
SSH tunneling allows you to securely forward traffic from one device to another. This can be especially useful for accessing services that are only available on the remote network, such as databases or internal web applications. To set up an SSH tunnel, use the following command:
ssh -L local_port:destination_host:destination_port username@remote_device_ip
SSH Automation
Automating SSH tasks can save you a ton of time and effort. Whether it’s running scripts, syncing files, or monitoring servers, there are countless ways to streamline your workflow. Tools like Ansible and Fabric can help you automate SSH-based tasks with ease.
Troubleshooting Common SSH Issues
Even the best-laid plans can sometimes go awry. If you’re having trouble with your SSH connections, here are a few common issues and how to fix them:
- Connection Refused: Check that the SSH service is running on the remote device and that the firewall allows incoming connections on the SSH port.
- Authentication Failed: Verify that your SSH keys are correctly configured and that your username and password are correct.
- Timeout Errors: Ensure that your network connection is stable and that there are no routing issues between your local machine and the remote device.
By addressing these issues, you can quickly resolve most SSH-related problems and get back to work.
Alternatives to SSH
While SSH is a powerful tool, it’s not the only option for remote access. Here are a few alternatives to consider:
- TeamViewer: A user-friendly remote desktop solution that’s great for non-technical users.
- VNC: Another popular remote desktop protocol that offers more customization options.
- Remote Desktop Protocol (RDP): A Microsoft-developed protocol that’s widely used in corporate environments.
Each of these alternatives has its own strengths and weaknesses, so it’s important to choose the one that best fits your needs.
Benefits of Using SSH for Remote Login
Now that you know how SSH works and how to set it up, let’s talk about the benefits. Here are just a few reasons why SSH is the go-to choice for remote access:
- Security: SSH provides strong encryption and authentication to protect your data.
- Flexibility: SSH works with a wide range of devices and operating systems, making it a versatile tool.
- Efficiency: With SSH, you can automate tasks, transfer files, and manage servers with ease.
Whether you’re a tech-savvy professional or a casual user, SSH offers something for everyone.
SSH Device from Anywhere Login Explained
One of the coolest features of SSH is the ability to log in to your devices from anywhere in the world. All you need is an internet connection and the right credentials. Here’s how it works:
First, make sure your remote device is configured to accept SSH connections. This usually involves enabling SSH in the settings and opening the necessary ports on your router. Next, set up port forwarding to direct incoming SSH traffic to your device. Once everything is configured, you can connect to your device from anywhere using its public IP address.
Of course, there are a few things to keep in mind. Make sure to secure your connections with strong authentication methods and regularly update your SSH software to protect against vulnerabilities. With these precautions in place, you’ll be able to access your devices from anywhere with confidence.
Wrapping It All Up
SSH device from anywhere login is more than just a tool; it’s a gateway to a more connected and productive world. By mastering SSH, you can unlock the full potential of remote access and take control of your digital life. From setting up secure connections to troubleshooting common issues, this guide has provided you with the knowledge and tools you need to succeed.
So, what are you waiting for? Dive into the world of SSH and see how it can transform the way you work. And don’t forget to share your experiences and tips with the community. Together, we can make remote access safer, easier, and more efficient for everyone.
Until next time, stay connected and stay secure!