Hey there, tech enthusiasts! If you're reading this, chances are you've stumbled upon a tricky situation where you need to access RemoteIoT behind a firewall on your Mac but don't know where to start. Don’t worry—we’ve got your back! Whether you're working remotely, managing IoT devices, or just trying to stay connected, this guide will walk you through every step of the process. Let’s dive in!
Let’s face it—firewalls can be a real pain in the neck, especially when you’re trying to connect to something as crucial as RemoteIoT. But here’s the good news: with the right tools, techniques, and a little bit of patience, you can bypass those pesky restrictions like a pro. This article isn’t just another tech jargon-filled walkthrough; it’s your ultimate cheat sheet for getting things done without losing your mind.
In today’s digital age, being able to access your IoT devices from anywhere is more important than ever. From home automation to industrial monitoring, RemoteIoT has become an essential tool for many. But what happens when your network is locked down tight? That’s exactly why we’re here—to help you navigate the tricky waters of firewalls and get your Mac talking to the outside world.
Read also:Reid Gray Florida New Wife The Untold Story
Understanding Firewalls and Why They Exist
Before we jump into the nitty-gritty of how to use RemoteIoT behind a firewall, let’s take a step back and understand why firewalls exist in the first place. A firewall is basically a security system that controls incoming and outgoing network traffic based on predetermined rules. Think of it as a bouncer at a club—only the people (or data packets) with the right credentials get in.
Firewalls are designed to protect your network from unauthorized access, but sometimes they can be overly restrictive. This can create problems when you’re trying to connect to services like RemoteIoT that require open access. So, how do you strike a balance between security and functionality? That’s what we’ll explore in the sections below.
Types of Firewalls You Might Encounter
- Network Firewalls: These are the big boys, usually managed by your IT department or service provider.
- Software Firewalls: These are installed on individual devices, like your Mac, and can be customized to suit your needs.
- Cloud Firewalls: These are hosted in the cloud and can be configured remotely, making them a great option for remote workers.
Knowing which type of firewall you’re dealing with is crucial because it will determine the best approach to take. For example, if you’re dealing with a network firewall, you might need to work with your IT team to get the necessary permissions. On the other hand, if it’s a software firewall, you can often tweak the settings yourself.
Why RemoteIoT Matters
RemoteIoT is more than just a fancy buzzword—it’s a game-changer for anyone working with Internet of Things (IoT) devices. Whether you’re monitoring smart home gadgets, managing industrial equipment, or running a fleet of connected devices, RemoteIoT allows you to access and control them from anywhere in the world.
But what makes RemoteIoT so special? Here are a few reasons:
- Real-Time Data Access: Get instant updates on the status of your devices without any lag.
- Centralized Control: Manage multiple devices from a single dashboard, making your life infinitely easier.
- Security: With advanced encryption and authentication protocols, RemoteIoT ensures your data stays safe.
So, whether you’re a tech-savvy homeowner or a professional engineer, RemoteIoT is a tool you don’t want to miss out on. And with the right techniques, you can use it even behind a firewall.
Read also:Expedition Unknown Josh Gates Hospitalized Ndash What Really Happened
How to Use RemoteIoT Behind Firewall on Mac
Now that we’ve covered the basics, let’s get down to business. Here’s a step-by-step guide on how to use RemoteIoT behind a firewall on your Mac:
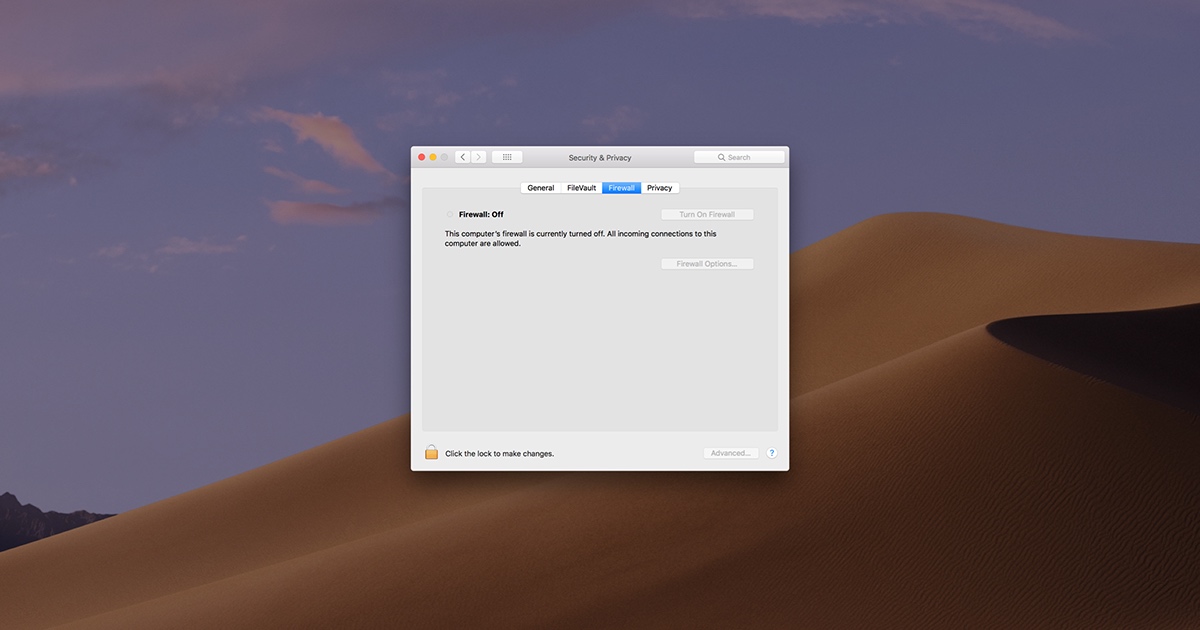
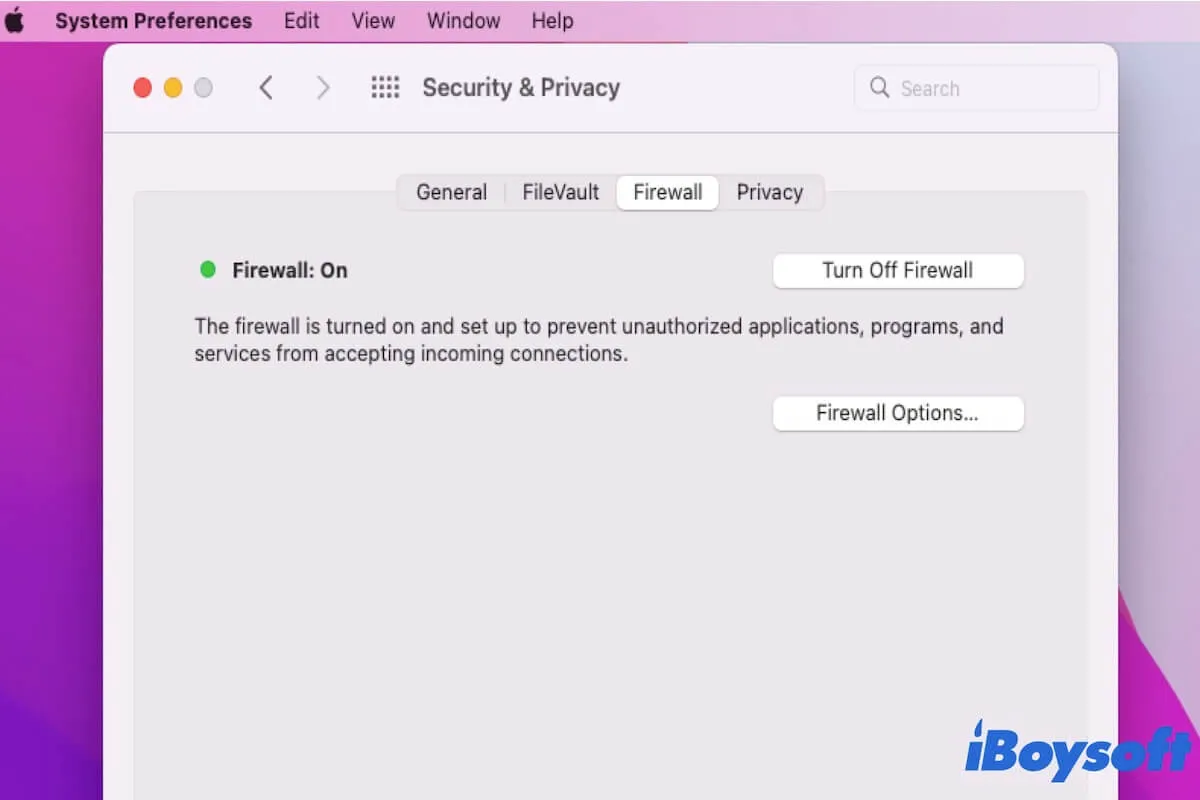
Step 1: Check Your Firewall Settings
The first thing you need to do is figure out what kind of firewall you’re dealing with. If it’s a software firewall, you can usually access the settings through your system preferences. Look for any rules that might be blocking RemoteIoT and adjust them accordingly.
If it’s a network firewall, things get a bit trickier. You’ll need to work with your IT team to whitelist the necessary ports and IP addresses. This might involve filling out some paperwork or attending a meeting, but trust us—it’s worth it.
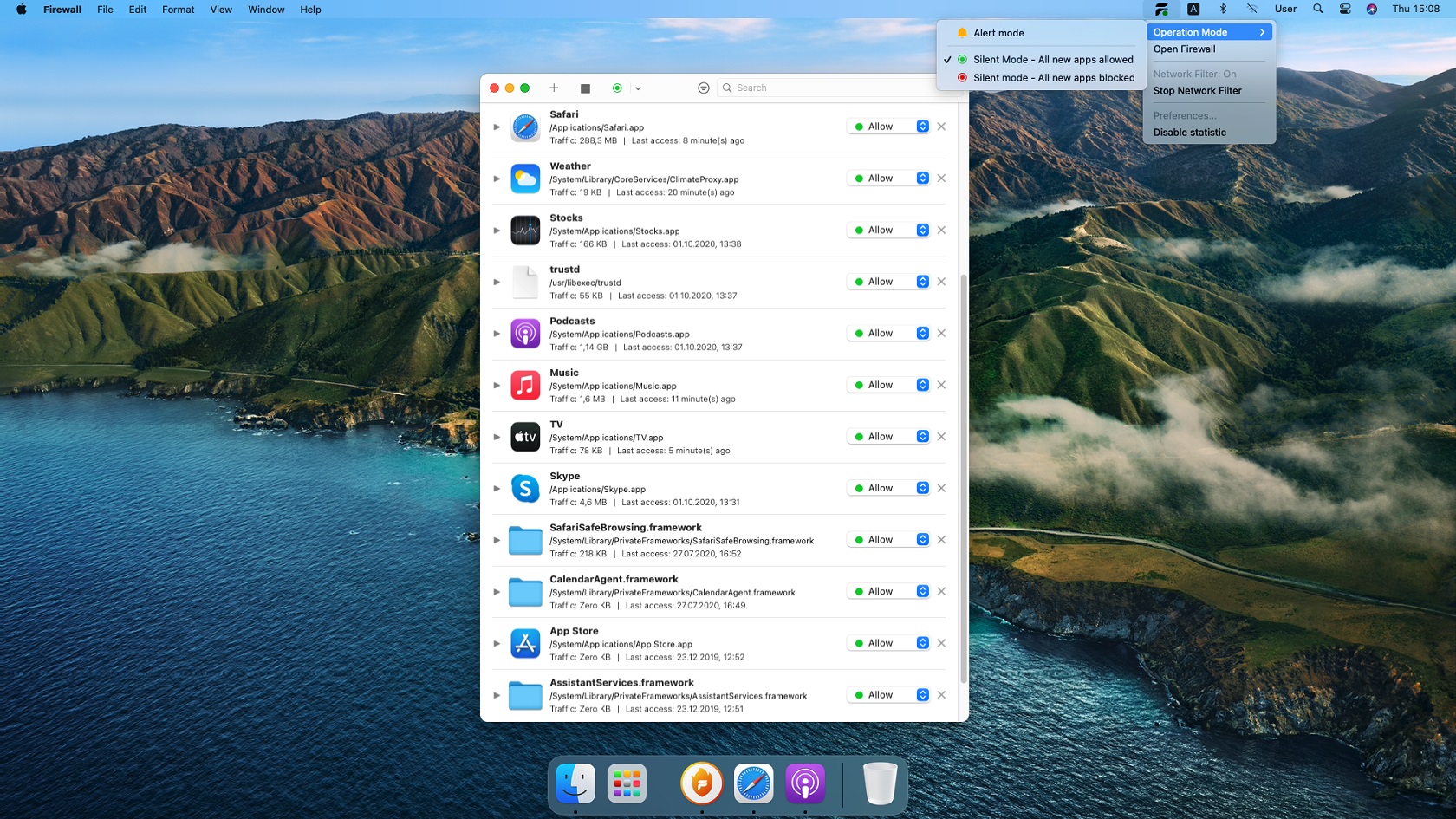
Step 2: Use a Proxy Server
A proxy server acts as an intermediary between your Mac and the internet, allowing you to bypass certain restrictions. There are several proxy servers available, both free and paid, that you can use to access RemoteIoT behind a firewall. Some popular options include:
- Squid Proxy
- Privoxy
- CCProxy
Just remember to choose a reputable provider to ensure your data stays secure.
Step 3: Configure Port Forwarding
Port forwarding is another effective way to bypass firewalls. It involves directing incoming traffic to a specific port on your Mac, allowing you to access RemoteIoT without any issues. Here’s how you can set it up:
- Open your router’s admin page and log in with the appropriate credentials.
- Locate the port forwarding section and add a new rule.
- Specify the port number and IP address of your Mac.
While this might sound complicated, most modern routers have user-friendly interfaces that make the process a breeze.
Common Issues and Solutions
Even with the best-laid plans, things can sometimes go wrong. Here are some common issues you might encounter when trying to use RemoteIoT behind a firewall, along with their solutions:
Issue 1: Connection Timeout
Solution: Check your firewall settings to ensure that the necessary ports are open. If you’re using a proxy server, make sure it’s configured correctly.
Issue 2: Authentication Failed
Solution: Double-check your login credentials and make sure they match the ones you’re using for RemoteIoT. If you’re still having trouble, try resetting your password.
Issue 3: Slow Performance
Solution: Optimize your network settings and consider upgrading your internet connection if possible. You might also want to look into using a faster proxy server.
Best Practices for Using RemoteIoT Behind Firewall
Now that you know how to use RemoteIoT behind a firewall, let’s talk about some best practices to keep in mind:
- Stay Secure: Always use strong passwords and enable two-factor authentication wherever possible.
- Regularly Update: Keep your software and firmware up to date to protect against vulnerabilities.
- Monitor Activity: Keep an eye on your network traffic to detect any suspicious activity.
By following these best practices, you can ensure that your RemoteIoT setup remains secure and reliable.
Tools and Resources to Help You Along the Way
There are plenty of tools and resources available to help you use RemoteIoT behind a firewall. Some of our favorites include:
- Wireshark: A powerful network analysis tool that lets you inspect and analyze network traffic.
- Tailscale: A secure mesh networking solution that makes it easy to connect devices behind firewalls.
- Tor: An anonymous browsing tool that can help you bypass certain restrictions.
These tools can save you a lot of time and effort, so don’t hesitate to explore them further.
Real-World Examples and Case Studies
To give you a better idea of how RemoteIoT can be used behind a firewall, let’s look at a couple of real-world examples:
Example 1: Smart Home Automation
John, a tech-savvy homeowner, wanted to access his smart home devices from work. By configuring his firewall settings and using a proxy server, he was able to control his lights, thermostat, and security system from anywhere in the world.
Example 2: Industrial Monitoring
Susan, an engineer at a manufacturing plant, needed to monitor critical equipment remotely. With the help of port forwarding and a secure connection, she was able to keep an eye on her machines and ensure smooth operations.
These examples demonstrate the versatility and power of RemoteIoT, even in challenging environments.
Conclusion and Call to Action
And there you have it—a comprehensive guide on how to use RemoteIoT behind a firewall on your Mac. From understanding firewalls to configuring port forwarding, we’ve covered everything you need to know to get the job done. Remember, the key is to stay patient, persistent, and proactive.
So, what are you waiting for? Take action today and start exploring the world of RemoteIoT. Don’t forget to share your experiences in the comments below or check out our other articles for more tech tips and tricks. Happy connecting!
Table of Contents
- Understanding Firewalls and Why They Exist
- Types of Firewalls You Might Encounter
- Why RemoteIoT Matters
- How to Use RemoteIoT Behind Firewall on Mac
- Step 1: Check Your Firewall Settings
- Step 2: Use a Proxy Server
- Step 3: Configure Port Forwarding
- Common Issues and Solutions
- Best Practices for Using RemoteIoT Behind Firewall
- Tools and Resources to Help You Along the Way
- Real-World Examples and Case Studies