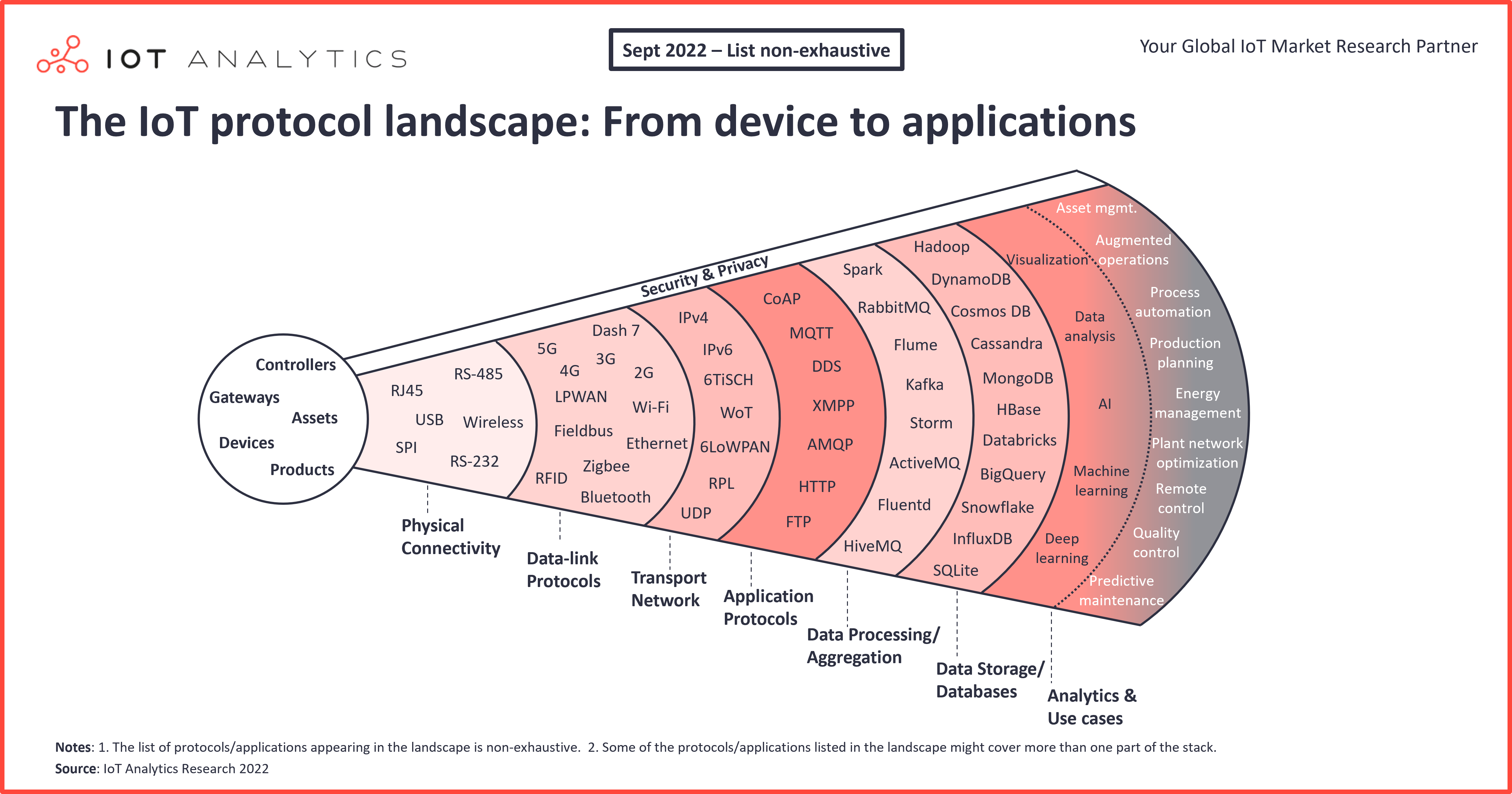
When it comes to securing your IoT devices, SSH is one of the most reliable tools you can use. But not all SSH implementations are created equal. To protect your network and ensure smooth operations, you need to know the best IoT SSH practices. In this guide, we’ll dive deep into what makes an IoT SSH setup truly secure and efficient.
Imagine this: you’ve got a bunch of IoT devices connected to your network, and you want to manage them remotely without worrying about hackers sneaking in. That’s where SSH comes into play. It’s like having a secret handshake that only authorized users can use to access your devices. But hey, just setting up SSH isn’t enough—you need to do it right.
From configuring firewalls to using strong authentication methods, we’ll cover everything you need to know about the best IoT SSH practices. Whether you’re a tech enthusiast or a professional managing a large-scale IoT network, this guide has got your back.
Read also:Emilys Diary Ep 16 A Deep Dive Into The Latest Episode Thats Got Everyone Talking
Table of Contents
- What is SSH?
- IoT SSH Basics
- Best IoT SSH Practices
- Security Tips for IoT SSH
- Common Mistakes to Avoid
- SSH Alternatives for IoT
- Performance Optimization for IoT SSH
- Remote Management with IoT SSH
- Scaling IoT Networks with SSH
- Conclusion
What is SSH?
SSH, or Secure Shell, is like the superhero of remote access protocols. It’s designed to give you a secure way to connect to devices over a network, even if that network isn’t super safe. Think of it as a secure tunnel that keeps prying eyes out while you’re managing your IoT devices.
SSH encrypts all communication between your computer and the IoT device, making it nearly impossible for hackers to intercept sensitive data. And here’s the kicker—it doesn’t just stop at encryption. SSH also offers authentication mechanisms to make sure only the right people can access your devices.
But why is SSH so important for IoT? Well, with more and more devices getting connected every day, the risk of cyberattacks is higher than ever. SSH provides that extra layer of security to keep your IoT network safe and sound.
IoT SSH Basics
Alright, let’s get down to the basics. When you’re dealing with IoT devices, SSH is one of the best ways to manage them remotely. But before you jump in, there are a few things you need to know.
First off, not all IoT devices support SSH out of the box. Some might require additional configuration or even custom firmware. So, it’s important to check if your devices are SSH-compatible before you start setting things up.
Once you’ve got that sorted, the next step is to configure SSH on your devices. This usually involves setting up a username and password, or better yet, using SSH keys for authentication. Trust me, SSH keys are the way to go—they’re way more secure than passwords.
Read also:Did Kaylee Hartung Have Eye Surgery Unveiling The Truth Behind The Speculation
Setting Up SSH on IoT Devices
Setting up SSH on your IoT devices isn’t as complicated as it sounds. Here’s a quick rundown of what you need to do:
- Enable SSH on your IoT device. Most devices will have this option in their settings menu.
- Create a strong password or generate an SSH key pair for authentication.
- Configure your firewall to allow SSH traffic. By default, SSH uses port 22, but you can change this if you want to add an extra layer of security.
- Test your connection to make sure everything’s working smoothly.
And just like that, you’ve got SSH up and running on your IoT devices. Easy peasy, right?
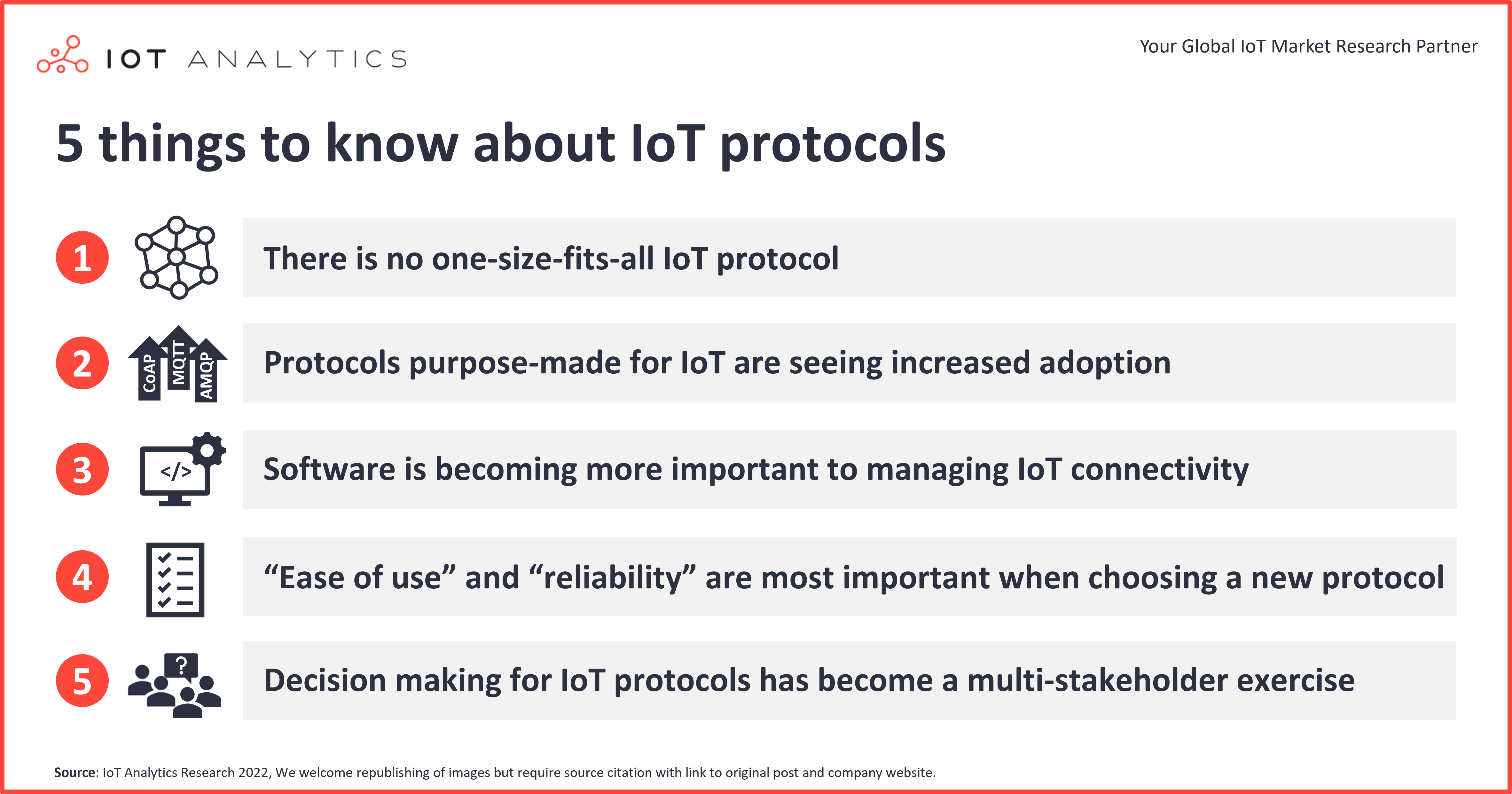
Best IoT SSH Practices
Now that you know the basics, let’s talk about the best IoT SSH practices. These tips will help you secure your network and ensure that your IoT devices are running smoothly.
First things first, always use SSH keys instead of passwords. Passwords can be easily guessed or cracked, but SSH keys are much harder to break. Plus, they’re way more convenient—you don’t have to remember a bunch of complex passwords.
Another important practice is to keep your SSH software up to date. Just like any other software, SSH has its vulnerabilities, and updates often include security patches to fix those issues. So, make sure you’re running the latest version of SSH on all your devices.
Firewall Configuration for IoT SSH
Firewalls are your first line of defense against unauthorized access. When it comes to IoT SSH, configuring your firewall properly is crucial. Here are a few tips:
- Restrict SSH access to specific IP addresses if possible. This limits who can connect to your devices.
- Change the default SSH port (22) to something less common. This makes it harder for hackers to find your SSH service.
- Set up rate limiting to prevent brute-force attacks. This will limit the number of login attempts someone can make in a given time period.
By following these firewall configuration tips, you can significantly reduce the risk of unauthorized access to your IoT devices.
Security Tips for IoT SSH
Security is always a top priority when it comes to IoT devices. Here are some additional tips to keep your SSH connections secure:
- Use two-factor authentication (2FA) whenever possible. This adds an extra layer of security by requiring a second form of verification in addition to your SSH key.
- Disable root login. Allowing root access over SSH is a big no-no. Instead, create a regular user account and use sudo for administrative tasks.
- Monitor your SSH logs regularly. This will help you detect any suspicious activity and take action before it becomes a problem.
These security tips might seem like a lot of work, but trust me, they’re worth it. A secure IoT network is a happy IoT network.
Common Mistakes to Avoid
Even the best of us make mistakes sometimes. Here are a few common mistakes to avoid when setting up IoT SSH:
- Using weak passwords. I can’t stress this enough—strong passwords are essential for security.
- Not changing default settings. Whether it’s the default SSH port or the default admin username, always change these settings to something unique.
- Ignoring software updates. Keeping your SSH software up to date is crucial for maintaining security.
By avoiding these common mistakes, you can save yourself a lot of headaches down the road.
SSH Alternatives for IoT
While SSH is one of the best tools for securing IoT devices, it’s not the only option. Depending on your specific needs, there are other protocols you might want to consider:
MQTTS
MQTTS is a secure version of the MQTT protocol, which is commonly used for IoT communication. It provides encryption and authentication similar to SSH but is designed specifically for IoT devices.
COAPS
COAPS is another secure protocol for IoT devices. It’s based on the CoAP protocol and adds encryption and authentication to make it more secure.
Both MQTTS and COAPS are great alternatives to SSH if you’re looking for something more lightweight or better suited to specific IoT use cases.
Performance Optimization for IoT SSH
Performance is just as important as security when it comes to IoT SSH. Here are a few tips to optimize your SSH connections:
- Use compression to reduce the amount of data being transferred. This can help improve connection speed, especially over slower networks.
- Limit the number of open connections. Too many open connections can slow down your network, so it’s a good idea to set a limit.
- Optimize your SSH configuration file. By tweaking settings like the cipher and key exchange algorithms, you can improve performance without sacrificing security.
By following these performance optimization tips, you can ensure that your IoT SSH connections are both secure and efficient.
Remote Management with IoT SSH
One of the biggest advantages of using SSH for IoT devices is the ability to manage them remotely. Whether you’re troubleshooting a problem or updating firmware, SSH makes it easy to do everything from the comfort of your own home.
But remote management isn’t just about convenience—it’s also about security. By using SSH, you can ensure that your management activities are secure and protected from prying eyes.
Best Tools for Remote Management
There are a few tools that can make remote management with SSH even easier:
- SSH clients like PuTTY or OpenSSH. These tools provide a simple interface for connecting to your IoT devices.
- Monitoring tools like Nagios or Zabbix. These tools can help you keep an eye on your IoT devices and alert you to any issues.
With the right tools, remote management becomes a breeze.
Scaling IoT Networks with SSH
As your IoT network grows, managing all those devices can become a challenge. SSH can help you scale your network efficiently by providing a secure and reliable way to manage multiple devices at once.
One approach to scaling is to use a centralized SSH server. This server can act as a gateway to all your IoT devices, making it easier to manage them from a single location. Just make sure your server is secure and properly configured to handle the load.
Conclusion
So, there you have it—the best IoT SSH practices for securing and managing your IoT devices. From setting up SSH on your devices to optimizing performance and scaling your network, we’ve covered everything you need to know.
Remember, security is key when it comes to IoT. By following the tips and practices outlined in this guide, you can ensure that your IoT network is both secure and efficient. And don’t forget to keep an eye on those software updates—they’re crucial for maintaining security.
Now it’s your turn. Have you tried implementing any of these best IoT SSH practices? Let us know in the comments below. And if you found this guide helpful, don’t forget to share it with your friends and colleagues. Together, we can make the IoT world a safer place!